USER-CHI takes a closer look at cybersecurity and data protection in electric charging
With more and more aspects of life moving into the digital sphere, cybersecurity and protection of personal data are topics more important than ever. Even electric mobility cannot avoid this discussion. To address the topic from the point of view of electric charging infrastructure, the USER-CHI colleagues from IKEM, who are also co-leading the ethics committee of the project, prepared a webinar Cybersecurity and data protection in electric mobility. Annika Weber, a research associate from IKEM welcomed the participants in the webinar and explained the logic behind choosing the topic of cybersecurity: “In USER-CHI we develop a lot of smart solutions, and smart solutions in this case mean digital solutions. This means that, inevitably, data is collected and processed, which makes this topic a very relevant one for our project.”

In four presentations, the participants had the chance to get acquainted with the principles of data protection law, an overview of technical aspects of cybersecurity in mobility and 2 projects that addressed the topic under the umbrella of the Horizon2020 funding programme.
Data protection legal basis valid for electric charging
To get better insight into the legal framework, Simon Großmann, a research associate from IKEM shared a presentation about data protection and cybersecurity law, followed by a few implementation tips. Many authorities in both private and public sectors are limiting their use of data because they assume the data protection law does not permit them to do so, or they are not sure about the legal constraints, so they rather shy away from data-based projects. However, this is a huge limiting factor in today’s world. “The amount of data has increased fifty-fold since 2010 and AI and other emerging technologies are expected to generate unprecedented amount of data in the future”, said Simon during his presentation in the webinar. “Now it’s more important than ever to know at least the basics of data law.”
In his presentation, Simon explained the difference between public and personal data. He introduced some fundamental pieces of EU legislation, such as the European Data Act, Data Governance Act and GDPR. The participants also learned how these frameworks apply to electric charging, which data are collected during the charging process and what principles have to apply when processing them.
Addressing cybersecurity risks to electric charging infrastructure
The second presenter of the day was Dr Oihana Otaegui Madurga from the Transport and Security Division of VICOMTECH, a technological centre specializing in artificial intelligence, visual computing, and interaction. “We have exciting times ahead of us when looking at mobility”, said Oihana. “From autonomous driving to interoperability with electric smart charging, there are many new opportunities.”
However, according to Oihana’s research, the new public and private charging infrastructure also increases risks that have to be managed accordingly. “Among those risks, cybersecurity is one of the most important. It will be a crucial element of a resilient electric transportation network and system,” described Oihana during her presentation. She continued by explaining the reasons behind the vulnerability of electric mobility infrastructures to digital attacks, as well as the types of attacks that can occur. At the end of the presentation, the participants learned about the various cybersecurity layers applied to the vehicles, infrastructure and communication between the different parts of the ecosystem, as well as about some best practices in the field.
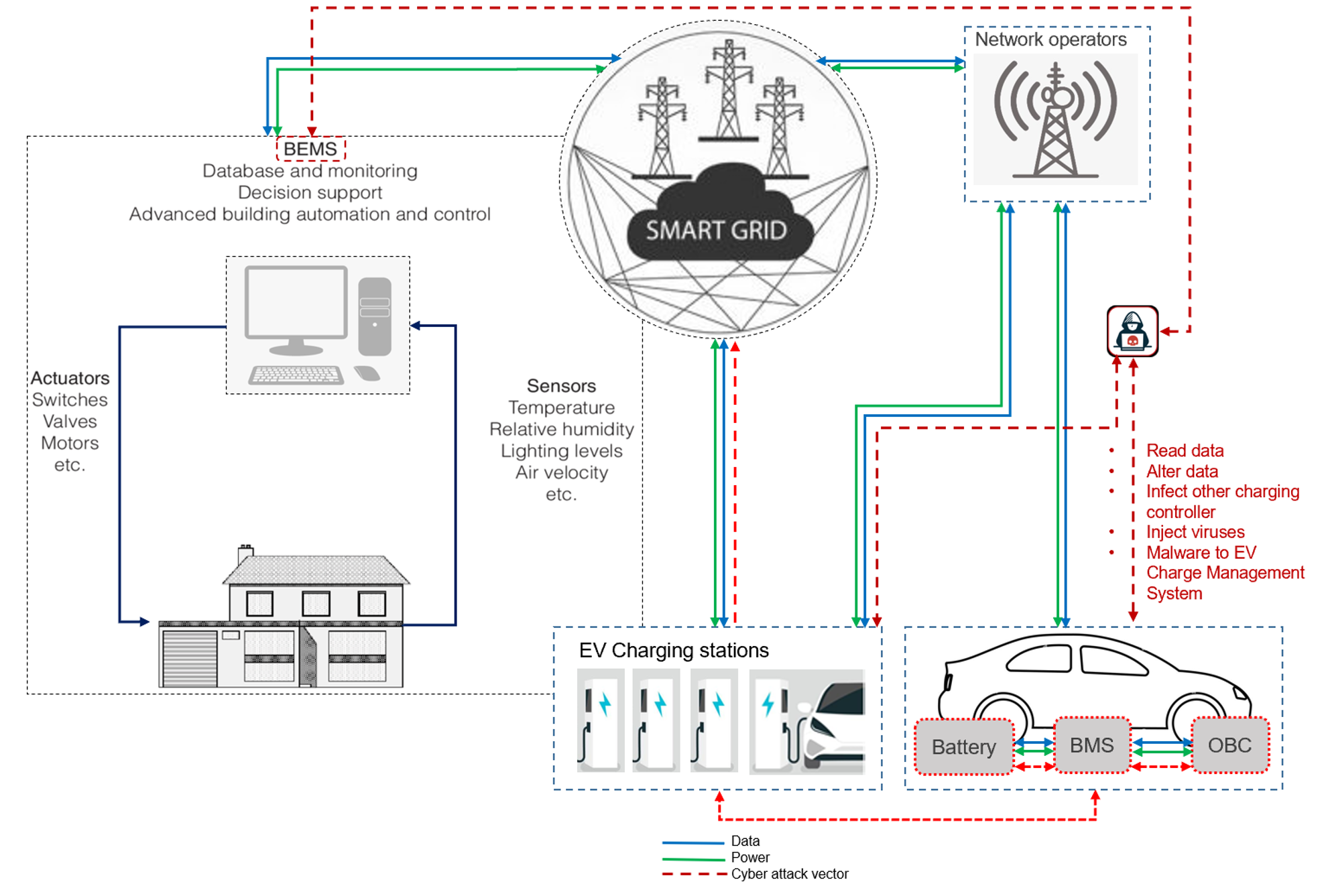
Typical Smart City Charging Infrastructure and Cyber Attack Vectors. Source: RESPONSE Horizon 2020 project
EU-funded projects bring research and solutions to the table
The second half of the webinar belonged to two Horizon 2020 EU-funded projects. The first of them, CARAMEL, was presented by Jordi Guijarro from i2CAT. CARAMEL was a project focusing on threads to connected vehicles. The project produced an anti-hacking device to be installed inside the autonomous and connected vehicles which uses machine learning techniques to mitigate various forms of digital attacks. During his presentation, Jordi showed the participants the demonstrations that occurred within the project, simulating different types of attacks on a vehicle.
One of the pillars of the project focused on smart charging abuse. Jordi explained to the participants the principles on which the product of CARAMEL project protects the grid from malfunctioning in the case of attack thanks to an anomaly detection technique. The presentation also touched upon the data protection challenges connected with the development and implementation of such technology.
The last presentation of the webinar was given by Dr. Inna Skarga-Bandurova, a Senior lecturer in artificial intelligence at the Oxford Brookes University who gave the participants an insight into the H2020 EU-funded project RESPONSE. “The project involves more than 70 innovative elements,” described Inna. “In the beginning, we analysed the potential service security threats for each of these components and we found out that some of the elements potentially present very high cybersecurity risk.” This was the case in particular for Automated driving and Vehicle-to-Vehicle communication via 5G, Fast Vehicle-to-Grid charging stations and EV charging schemes. In her presentation, Inna described the nature of threads relevant for the components developed in the project, such as the risk of interception of the communication between the vehicles, risk of unauthorised excess to sensitive data and manipulation of information which can lead to serious damage to the charging infrastructure and the grid. Inna also explained how they addressed these cybersecurity and data protection risks in the project through cybersecurity measures.
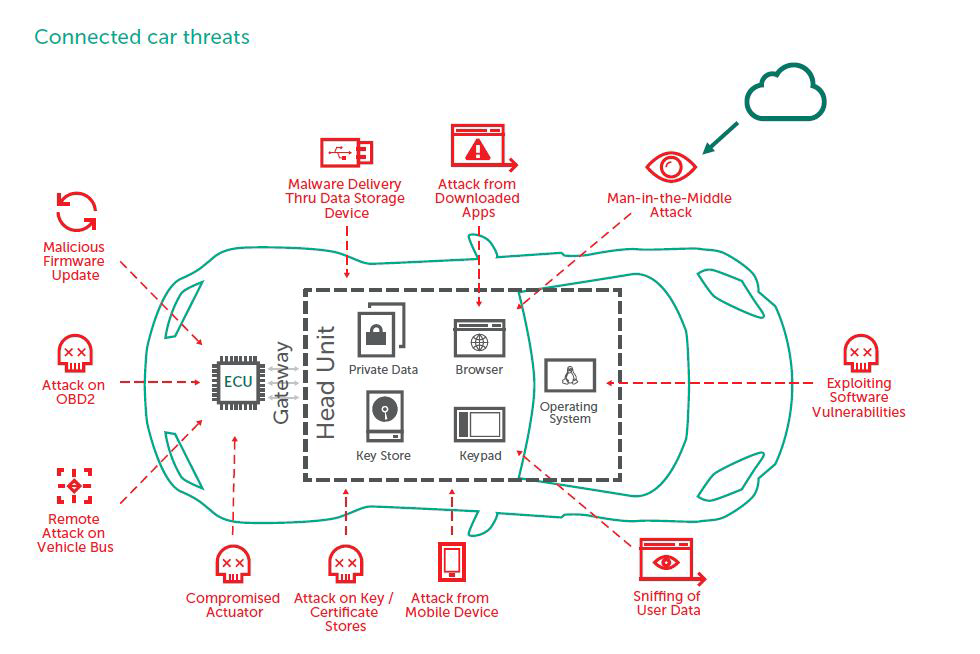
Potential cybersecurity threats to connected and automated vehicles. Source: CARAMEL H2020 project
After the presentations, all 4 speakers engaged in a discussion revolving around the ever-changing and evolving nature of cybersecurity threats and attacks and the ways how to react to those developments in real-time. It was clear that the webinar addressed a very timely topic and that there will be a lot more research and developments in the future.





